By R.K. Gardner, New World Technology Partners |
Digital technology, often expressed as Information and Communications Technology (ICT) embodies a more expansive and vulnerable array of elements than has been considered in traditional cyberspace. The pace of introduction and (often hasty) adoption of new and emerging technologies, applications and information artifacts, upon which enterprises and government institutions/agencies rely to conduct business, has become a global system-of-systems, composed of numerous interdependent components and myriad channels. They operate in a rapidly changing socio-political environment that presents threats from individual, group and state actors with shifting alliances, attitudes and agendas.
The ICT ecosystem includes many technologies that create, modify, process, communicate or control information. It includes Digital Computers, Quantum Computers, Signal Processors, Broadband (5G) Networks, Control Systems, Cryptography, AI and the new breed of microchips that power them. Their applications, often employing new technologies themselves, provide or assist enterprise or personal endeavors, including Supply Chain/3rd Party Management, Cloud, Privacy, SCADA/IoT, Fintech and more.
This risk mosaic presents a twofold challenge:
- Coping with the increasing threat-space offering so many accessible cyber targets
- Enabling emergent, systemic risks from the real-time interconnectedness of so many heterogeneous systems
Complexity is the new cyber adversary 1
In 2003, a series of (what should have been) minor failures in the electric power grid in Ohio set off a spectacular power outage that propagated beyond Ohio and through the entire Northeast region of the country, leaving millions without power and bringing major cities to a complete standstill. This destructive event was carried and amplified by small, unnoticed instabilities in the heterogeneous control systems of the power grid, each of which individually operated correctly.2 Similarly, in 2009, a Czech Internet backbone router advertised a very long route path that couldn’t be handled by routers running legacy software, causing a cascade of events wherein old routers repeatedly shut down and rebooted, saturating the system with traffic and causing Internet disruptions around the globe3.
What do these failures have in common? There were no nefarious adversarial actors to defend against; the complex, heterogeneous nature of the systems themselves led to emergent behaviors—behaviors that cannot be predicted by examining individual components but are rather produced by the system as a whole—facilitating “perfect storms” that conspired to enable these catastrophes.
The complexity of cyber ecosystems is not one-dimensional—it comprises numerous hardware, software and communication subsystems, as well as an unplanned combination of legacy and new systems haphazardly integrated over many years. Software industry assessments also tell us to expect a software defect density (code error rate) of one flaw per 1,000 lines of code on average, contributing to these complex dynamics that can interact in unexpected ways4.
Moreover, today’s well-informed adversaries could identify fragility in our critical infrastructure and exploit it with seemingly harmless or hardly visible intrusions. Modern threat detection software does not seek or detect these system conditions, leaving them highly vulnerable and allowing the system itself to do the hard work of propagating attack consequences.
Technology Complexity has, in effect, become a new adversary!
The complexity adversary does not require outside assistance; it can be summoned by minor user, environmental or equipment failures, or even quirks and architectural instabilities in the ordinary operation of the system. Enterprises anxious to benefit from the price, performance and competitive advantages promised by new technology are hastily constructing what are known as “complex adaptive system-of- systems” where their behavior cannot be predicted by the behavior of the individual systems or components. The perfect breeding ground for emergent, systemic risks!
What’s at stake?
Whereas digital technology has grown from the electronic filing cabinet of the 1950s to the central nervous system of today’s enterprises and institutions, so too have the consequences changed from the purview of the data center manager to the Board of Directors. More than interruptions of operations and (income statement) cost of servicing breaches, technology risk consequences roll up to significant earnings, capital, stock value/volatility risks that are the domain of Enterprise Risk Management.
Emergent risks or systemic risks, which have significant and direct financial impact, also allow the public, partners/allies, and legislators which present additional risk amplifiers from compromised trust and reputation. In the current 24-hour news and social media environment, reputation risk is presenting second order consequences affecting not only sales, but investments (or government appropriations), authorities, partnership and alliance cooperation, even workforce recruiting/retention. Adversaries use and instigate breach news to fund themselves by the news itself which enables “day trading” to exploit the share volatility that frequently accompanies a newsworthy breach.
What can be done?
We cannot stop all breaches, deter adversaries nor afford to fund all needed security protections.
We can, however, survive if we examine our technology ecosystem with a wide-angle lens and Quantify Enterprise Risk consequences in well-understood financial, mission and reputation/trust consequences. Concatenate attack propagation analyses in a Risk Line-of-Sight model, as illustrated:
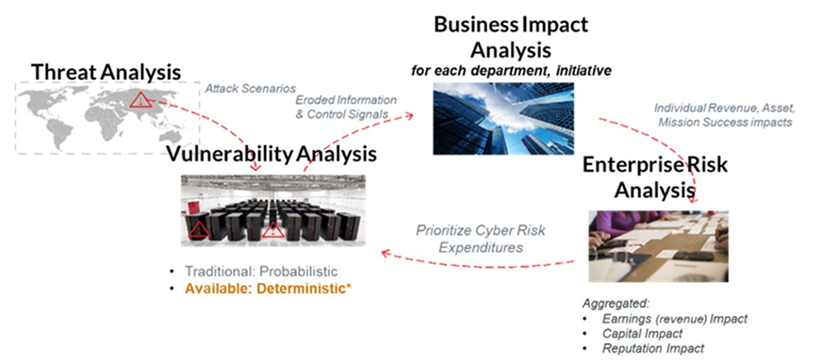
Image courtesy of New World Technology Partners.
ERM drives allocation of expenditures and capital reserves commensurate with exposure, enabling enterprise risk triage:
- Among and between high impact and low impact (acceptable) technology risks
- Among and between technology and non-technology enterprise operational risks
Further…
- System engineers can adjust for resilient architectures to evolve truly resilient systems that trap breaches, prevent system propagation and continue operating (absorb “rope-a-dope” punches and defeat your tired, spent adversary – Muhammad Ali)
- Analysts can anticipate hidden, systemic risks (skate where the puck will be – Wayne Gretzky) by integrating digital system behavior models with actors’ emergent behavior models (technologies and methodologies are available).
Summary
Beyond the risks from highly motivated, financed and capable adversaries, today’s technology risk mosaic harbors risks from the accretion of the hasty adoption and the complexity consequences we enable.
Analyze technology eco-systems with a wide-angle lens…
- to quantify enterprise consequences
- to anticipate and manage risks commensurate with exposure
- to evolve system architectures for truly resilient operations
Apply measured, incremental adoption, connection and commissioning of new technology
- use Rigorous Authentication (a la Zero Trust Networking)
- use Software Defined Networks (for critical connections)
Author:
- Robert “Bob” Gardner, NEW WORLD TECHNOLOGY PARTNERS
Compliments of New World Technology Partners – a member of the EACCNY.
![European American Chamber of Commerce New York [EACCNY] | Your Partner for Transatlantic Business Resources](https://eaccny.com/wp-content/uploads/2020/06/eaccny-logo.png)